Medical device manufacturers develop some of the most valuable intellectual property (IP) in the world. Protecting that IP is difficult, because it is often targeted by the most skilled adversaries in the world. Foreign governments, competitors and trusted employees all have the motive to steal the information, and traditional security approaches focused on the perimeter are unlikely to protect it. Before I detail steps that organizations can take to protect their IP, let me begin with a story.
When I led a managed security services practice, we had a large medical device manufacturer as a client. They were working on a next-generation auto-injector. They had invested $300 million in the technology, and they predicted it would generate $5 billion in revenue over the life of the patent. As part of their data protection program, the VP of engineering had worked with our team to identify and protect the information that was material to the product.
A few months later, our team noticed some strange behavior related to the identified information. A contractor had transferred a file that was by itself trivial to a removeable media device. A few days later, the same individual transferred another file that was trivial by itself but matched the policy via the drafts folder of his Gmail account. In the coming weeks, we saw more transfers of small amounts of protected information over various channels. We notified our counterparts in the client organization, and they developed a plan.
They told the contractor that the IT team had identified their may be a virus on his laptop and asked him to come in to have the virus removed. The employee did not come in as requested, and we started seeing massive transfers of files to several removeable media devices. The client immediately notified the authorities that they may be experiencing IP theft. The contractor was arrested by the FBI at Newark Liberty Airport and was sentenced to 10 years in federal prison. During the trial, it was found that he had previously stolen similar information from my client’s two biggest competitors when he was contracting with them—but had gotten away with it.
Traditional security programs focused on malware and perimeter security would have been blind to this threat because the threat had valid login credentials and was a trusted member of the team. He had legitimate access to the information and did not need to hack into anything. In fact, most of the biggest IP theft cases I have seen follow a similar pattern.
For example, in the Uber and Waymo case, a case of corporate espionage, the individual who allegedly stole the information was a trusted employee who then took the information to a new company owned by a competitor of his original company. In the American Semiconductor case, an American company was targeted by Sinovel, a Chinese company that was their customer. The theft was the result of a trusted employee being paid $2 million to steal information he could access. Time and time again, we learn that the adversary is a trusted employee stealing information for personal gain.
The truth is, IP is rarely stolen by “hackers”. The path of least resistance is generally targeting people with credentials. It matters not whether the credentials are compromised via phishing, or the people themselves are compromised through bribery or the promise of significantly better career opportunities. The point is the same. Protecting IP is not about keeping people out, it’s about identifying the information that is most important, the people who interact with that information, and having the ability to quickly identify deviations from normal behavior. Most security tools are useless against these types of attacks, but there are capabilities that help tremendously with protecting from these types of events.
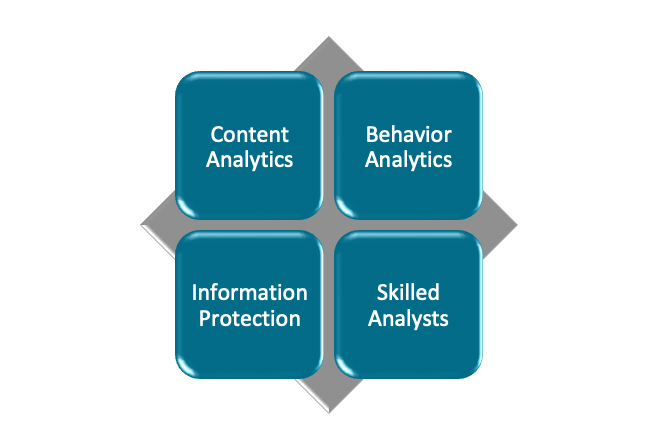
There are four disciplines that an organization must have to protect IP. The absence of any of these disciplines can lead to blind spots that can introduce risk, but they are not all created equal. You must have content analytics, behavior analytics, skilled analysts, and information protection, which lump together data classification and rights management strategies.
Content Analytics. Content analytics is the basis of IP protection. In most organizations, the simplest example is data loss prevention, but DLP systems are rarely enough by themselves. Content analytics, in this context, refers to the ability to identify critical information, such as IP, and protect it anywhere it travels, whether on premises or in the cloud. Most often, this will require multiple solutions working in concert to provide protection. This capability is foundational to IP protection because not all information is intellectual property, and in order to protect it, you must be able to distinguish the critical information from the commodity information.
Behavior Analytics. Behavior analytics is the next major element. Simply put, most IP theft that I have seen in the last decade is performed by someone with credentials in the environment. Sometimes those credentials are stolen, and sometimes the person has changed from a well-meaning insider to a malicious insider. Most security technologies focus on a specific method of attack and identifying or stopping that attack method. When dealing with a skilled human being, the methods of stealing data are infinite, so anticipating which method will be used is a fool’s errand. However, in order for a theft to occur, someone’s behavior must deviate from normal behavior. Whether it is from the user’s changing intent or the use of stolen credentials, in every case, it is possible to identify a change in behavior after the fact. Behavior analytics allows an organization to create a baseline of normal behavior to detect changes from that baseline.
Skilled Analysts. Next, organizations must have skilled analysts. Responding quickly and appropriately given the nature of the activity requires skills and experience. The reaction to a well-meaning insider should be different than the response to an external actor or a malicious employee. Treat a well-meaning insider like a malicious insider and you will alienate them. Treat a malicious insider like a well-meaning insider and you will alert them to your capabilities. They will simply find another way and you may or may not detect it.
Information Protection. Finally, information protection allows well-meaning insiders to protect information properly through the course of their business. Monitoring how your employees use these tools will help to determine intent. Malicious actors will not take extra time to protect information before stealing it. In fact, they may remove protections other users have put in place, providing an early red flag that the behavior analytics system can identify.
Protecting IP is not only possible, but vital for medical device manufacturers. Focusing a program around the four capabilities outlined in this article will help organizations protect their competitive advantages and their business.







