Register for the 2nd Annual Legacy Medical Device Cybersecurity Conference | A Virtual Event | September 22–23, 2020
We are standing right at the edge of entering to the Healthcare 4.0 era. Healthcare 4.0, which is represented by the Internet of Medical Things (IoMT) and big data analysis, brings connectivity and data-driven decision making to everyday healthcare practices. Nowadays, if you walk to an average North American hospital and look around, 48% of whatever equipment you see is connected. This number will reach 68% by 2023, according to Deloitte Consulting. The significant growth in the number of connected medical devices in the short to mid-term future is the unavoidable result of the prevalence of Internet of Things (IoT) in different industries, including healthcare and medical technology and science. IoMT is unfolding a new world of possibilities to improve the continuum of care. IoMT is beyond the single-loop linear 1:1 network-connected medical devices. It introduces the concept of an ecosystem comprising different components, technologies, applications, gadgets and programs that are connected to each other and to the internet through different endpoints, networks and nodes. This ecosystem forms a novel holistic healthcare platform encapsulating diagnosis, therapy and post-therapeutic surveillance, which will streamline the delivery of the healthcare, enhance customer satisfaction and improve accuracy of the key decision gates. In such a connected ecosystem, components communicate with each other in real-time and further with the users, generate and exchange data and big data, and send and receive commands and instructions.
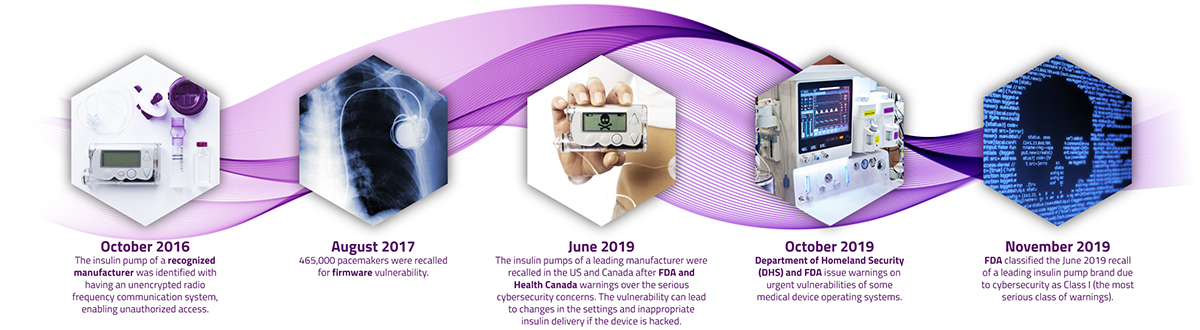
On the risk side, as the proliferation of connected and complex medical devices grows, healthcare providers are more susceptible to cyberattacks. This is already an all too common reality for many organizations in the healthcare space, the prominent ones are the exposed cyber vulnerabilities in insulin pumps and pacemakers of some leading manufacturers in recent years.1,2
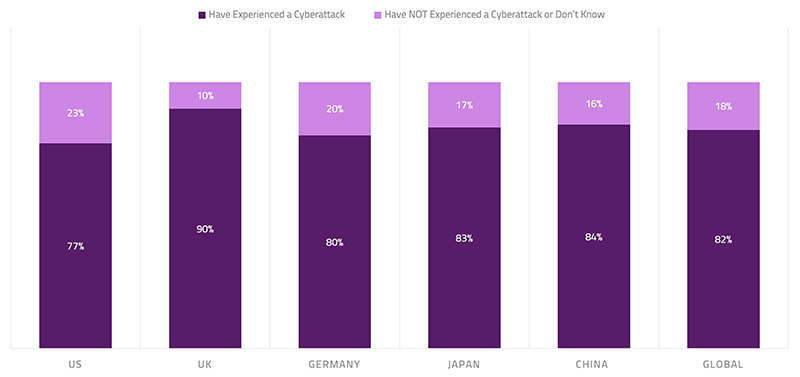
A recent survey found that 82% of healthcare organizations have experienced an IoT-focused cyberattack in the last year, with 30% of attacks resulting in compromised end-user safety. This alarming finding indicates that global care providers must continue to evolve their security approach to ensure the protection of care facilities, medical devices and the safety of patients. Not acknowledging cybersecurity as real as it is will put medical technology companies, healthcare practitioners (HCPs), and patients at identity theft or even health-related risks. The domain of the risk can be very extensive—i.e., from distorting the CT or endoscopy images to malfunctioning pacemakers and insulin pumps to tampering implantable or needle-based neuromodulators to holding medical devices hostage to stealing saved patient and user data on the device. Cyber threats can put stakeholders in significant financial and legal perils, which is small compared to the consequences of jeopardizing patient’s health and safety.
Major healthcare regulation policymakers across the world have started updating their pre-market cybersecurity requirements for medical devices to address, manage and lessen safety risks for users and patients. The 2018 FDA cybersecurity draft guidance puts forward a novel category for connected medical devices, Tier 1 and Tier 2, based on their connectivity and the scale of the harm they potentiate to carry if seized. Based on that, 510 (k) for Tier 1 devices should demonstrate documentation that the design and risk assessment activities precisely followed the FDA requirements. Other than this, it recommends a framework similar to NIST, proposes new labeling instructions and request companies to share a Cybersecurity Bill of Materials (CBOM) with customers.
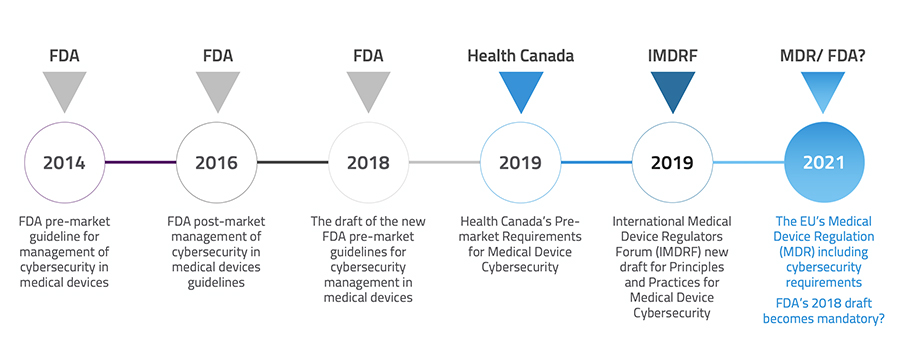
The EU MDR cybersecurity requirement, which has been postponed to 2021 due to the COVID-19 pandemic, sets up a framework of requirements called “defense-in-depth strategy” to ensure devices are secured from within. Both FDA and EU MDR highly emphasize incorporating and implementing a cybersecurity mindset from the very first steps of the product lifecycle to the end of support. With the new approach, patient safety due to the operation and performance of the equipment is weighed equally important as patient safety due to device cybersecurity.
FDA promotes medical manufacturers to design “Trustworthy” devices. According to FDA, trustworthy devices:
- Are reasonably secure from cybersecurity intrusion and misuse
- Provide a reasonable level of availability, reliability, and correct operation
- Are reasonably suited to performing their intended functions
- Adhere to generally accepted security procedures”.
The core purpose of trustworthy design is to outsmart and shift the traditional outside-in approach toward cybersecurity, which has historically been represented by network or endpoint security, and described as the job of the delivery organization, into an inside-out approach with the accent on device protection and manufacturer’s responsibility. Experience shows that endpoint security is not a holistic security strategy in the absence of appropriate protection for the rest of the ecosystem, and network security, however a must, but is crossable and cannot guarantee the security of platforms when connectivity is widespread across a large ecosystem.
The core outcome of the FDA trustworthy design and the EU’s defense-in-depth strategy is addressing those security risks with patient safety impact through maintaining, shielding and recovering the core functionality of a device. The core functionality of a regulated medical device is mainly responsible to deliver the labeled “Intended Use” (IU) and satisfy the approved “Indication For Use” (IFU), therefore anything that compromises the core functionality will eventually affect the IU. Defect in IU is not only an FDA label violation, but also projects a range of threats to patients and users starting from incompetency of the product to match with the claimed IFU to denial of service and even to serious safety risks for the caregiver and/ or patient. Looking from this angle, we can now realize why the FDA and other key policymakers across the world have been trying to update and strengthen the in-device cybersecurity measures to ensure core functionality protection at any cost.
New regulations can ultimately lead to having a more secure IoMT, however, device manufacturers might find it hard to assemble the needed resources and build up the essential infrastructures organically. Medical device manufacturers should transition their device cybersecurity approach from minimal and good-enough to secured by design through adopting the trustworthy framework and defense-in-depth strategy. The FDA views cybersecurity as a shared responsibility among companies, clinics, HCPs and patients. Therefore, medical device companies must consider cybersecurity as an indispensable requirement to their products and deliver education, training and support to customers and end-users to create and maintain a safe and secure ecosystem.
References
- FDA. (June 27, 2019). “FDA warns patients and health care providers about potential cybersecurity concerns with certain Medtronic insulin pumps”. Press Announcement. Retrieved from https://www.fda.gov/news-events/press-announcements/fda-warns-patients-and-health-care-providers-about-potential-cybersecurity-concerns-certain
- FDA. (August 29, 2017). “Firmware Update to Address Cybersecurity Vulnerabilities Identified in Abbott’s (formerly St. Jude Medical’s) Implantable Cardiac Pacemakers: FDA Safety Communication”. Retrieved from https://www.fda.gov/medical-devices/safety-communications/firmware-update-address-cybersecurity-vulnerabilities-identified-abbotts-formerly-st-jude-medicals






