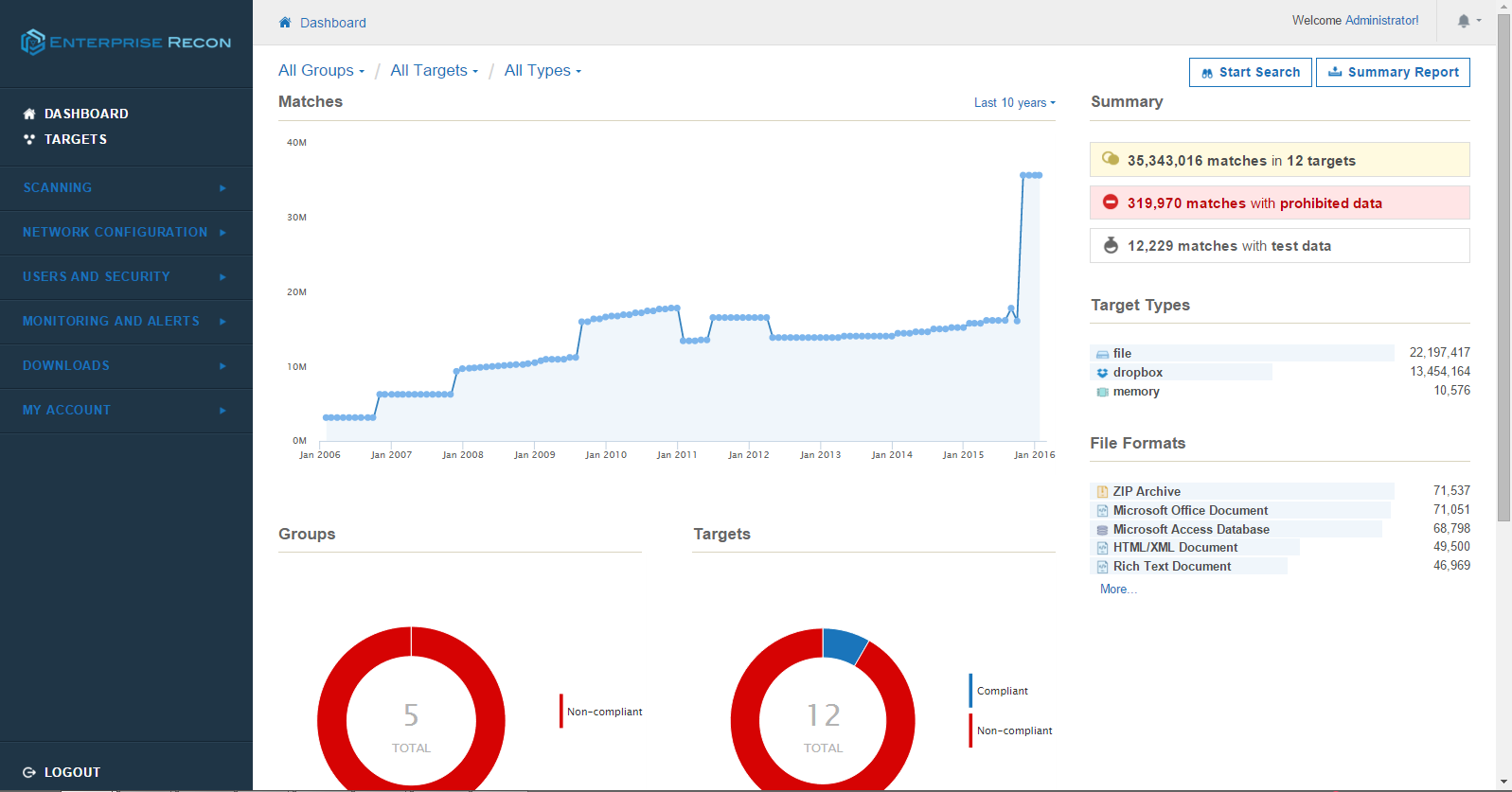
Medical device manufacturers play one of the most crucial roles in protecting patient information. As the incidence of cyberattacks continue to rise, device companies need to take a closer look at the design of interconnected systems, along with how and what kind of data they are collecting and transmitting through the healthcare system.
“There are a lot of different mechanisms for attacking devices, as seen with IoT, the Internet of Things, in particular. All of these devices are wide open and if you break it down and start looking at medical device manufacturers, it’s the same thing,” says John Wethington, vice president of Americas at Ground Labs, a sensitive data discovery and remediation software company. “In addition, firewalls don’t address the real problem—hackers are after the data.”

According to Wethington, in many cases healthcare providers do not have the expertise to address security needs, so ensuring that devices are secure out of the box is even more important. He suggests several best practices that device companies should implement to safeguard against vulnerabilities:
- Only collect information that is absolutely necessary. For example, many devices for diagnostics purposes collect ancillary information or metadata that isn’t essential for the provider or diagnosis. And in many cases, this information is stored in logs.
- Proper/secure coding practices should include security, not as an afterthought, but as a first priority.
- Ensuring proper data encryption and transmission.
- Requiring providers, when they communicate with devices, to do so in a secure manner. And if this is not the case, do not allow the information to be transmitted from the device.
- Making sure that device memory is properly cleaned. When a device is retired and resold, this sensitive data can be restored. Properly de-permissioning a device, along with resetting the system to ensure secure data deletion, is critical.
And as far as protecting patient information, Wethington expects a dramatic change in the regulatory landscape, which may include severe penalties for companies and more accountability placed on a company’s board of directors when data breaches occur. As a result, companies should be implementing processes now to try to get in front of potential vulnerabilities. “My hope is that security will become organic to an organization across the board, whether it’s the medical director, the product design engineer, the software developer or the support personnel,” says Wethington. “It has to be organic in the entire organization in order to be properly implemented. The biggest challenge is getting companies to see the threat and implement the appropriate policies and tools to make sure that they’re actually addressing them.”